There's a lot of chatter out there about how people find information, especially when it comes to what's called open source intelligence, or OSINT. It's a way of looking at publicly available details to put together a picture of something, or someone, or an event. And, you know, a big part of this work often involves social media, like Twitter, which some people now call X. It's really about being a good detective with information that's just out there for anyone to see, but then putting it all together in a smart way.
You might be wondering, what exactly does it mean to be an "OSINT defender" on a platform like Twitter? Well, it's pretty much about using these skills to protect yourself or others, or to just make sure the information you're getting is actually good. It's not always as simple as it seems, because, as a matter of fact, there's a lot of stuff out there that might not be quite right. So, people who are good at this kind of work, they tend to be really careful about what they share and what they believe, especially when it comes to what shows up on social media feeds.
So, we'll be talking a bit about how people use public information, what some of the tools are that help them, and why it's pretty important to be a bit cautious about certain things you see, particularly on places like Twitter. It’s about being smart with the details, you know, and making sure you're getting the full story, or at least a more accurate one. This is about being a savvy information user, which, in some respects, is a pretty useful skill for anyone these days.
Table of Contents
- What is OSINT, Anyway?
- How Do People Build Software with OSINT Defender Twitter?
- What Are Some Tools People Use for OSINT Defender Twitter Work?
- Social Media and OSINT Defender Twitter - What is the Connection?
- Public Perceptions of OSINT Defender Twitter Activity
- Legitimacy of OSINT Defender Twitter Accounts
- Finding Information on Twitter for OSINT Defender Twitter Tasks
- Tracking Accounts and OSINT Defender Twitter Tips
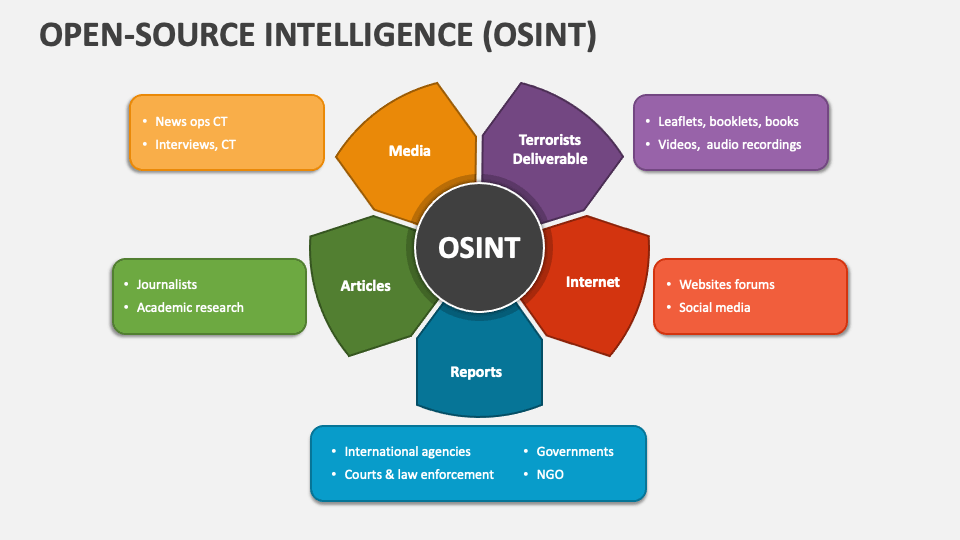
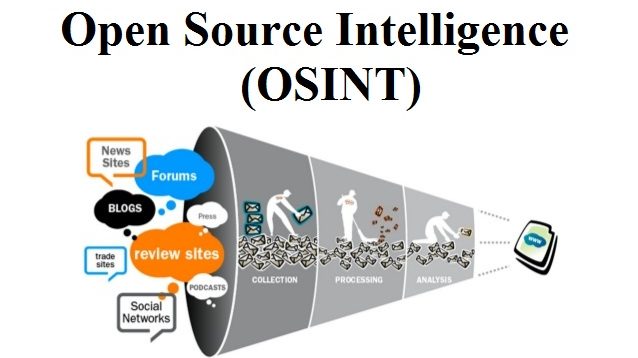
What is OSINT, Anyway?
When we talk about OSINT, which stands for open source intelligence, we are really talking about gathering information from sources that are, well, open. This means things that are publicly available, like articles, public records, social media posts, or even videos that anyone can see. It's not about breaking into anything or doing anything illegal; it's just about collecting and analyzing what's already out there. People use this for a whole bunch of different reasons, so it's a pretty broad area.
For example, some folks might use OSINT for information gathering in a general sense, just to learn more about a topic or a situation. Others might use it for things like cybersecurity, trying to figure out how a system might be vulnerable by looking at public details. It can also be pretty useful for what's called "reverse searching," which is like starting with a piece of information, say an image, and trying to find out where it came from or what it's connected to. So, it's a very versatile kind of skill, honestly, and it helps people piece together stories from what's openly shared.
Then there are those who use OSINT for things like "bug bounty" programs, where they look for weaknesses in software or systems to help companies fix them. It's also used for "trust and safety" work, which involves making sure online spaces are secure and free from bad actors. And, you know, some security teams, often called "red teams," use OSINT to test their own defenses by seeing what information they can gather about their organization from public sources. It's a way of thinking about how information flows, and how it can be used, for good or otherwise, you know.
- Album Cover Kanye West
- Pier 701 Restaurant Bar
- Lake Travis Water Level
- Crossstitchpk
- Anirudh Suswaram Indian Idol Latest
How Do People Build Software with OSINT Defender Twitter?
It's interesting to think about how much software gets built and shared these days, and a lot of that happens on a platform called GitHub. This is a place where people collaborate on code, share projects, and really just build things together. It's like a big online workshop for software developers. You see, more than 150 million people are using GitHub to find projects, make their own versions of them, and then add their own contributions to over 420 million different software projects. It's a truly massive collection of human effort, and, in a way, it shows how people work together to create tools that can be used for things like OSINT, even for those who consider themselves an OSINT defender on Twitter.
Some of the tools that are used for OSINT work, in fact, are open source themselves, meaning their code is available on platforms like GitHub. This means that people can look at how they work, suggest improvements, or even build on them to create new things. It’s a very collaborative environment, and it helps a lot of these information-gathering tools get better over time. For example, if someone creates a tool that helps with reverse searching, they might put it on GitHub so others can use it and help improve it. This kind of sharing is pretty important for the whole community, you know.
So, when you hear about a "curated list of amazingly awesome open source intelligence tools and resources," it often points back to places like GitHub. These lists bring together different software bits and pieces that help people with their OSINT work. They cover all sorts of areas, from gathering general information to more specialized tasks like cybersecurity analysis or even finding bugs in software. It's all about making these tools available and letting the community contribute to their development, which is, in some respects, how a lot of good software gets made these days, isn't it?
What Are Some Tools People Use for OSINT Defender Twitter Work?
There are, you know, quite a few specific tools that people mention when they talk about OSINT. One that comes up is a framework, or a set of tools working together, that helps gather details about things like phone numbers or email addresses. This kind of tool can also help with what's called "VIN OSINT," which means looking up information related to vehicle identification numbers. It can even perform tasks like finding subdomains related to a website. So, it's pretty comprehensive for gathering various bits of information, actually.
Another tool that gets talked about is Osintgram. As you might guess from the name, this is a tool specifically made for OSINT work on Instagram. It helps people collect information from that particular social media platform. Then there's Spiderfoot, which is a tool that automates a lot of the OSINT process. It's used for things like "threat intelligence," which means finding out about potential dangers, and also for "mapping your attack surface," which helps people understand where their digital systems might be vulnerable. It does a lot of the heavy lifting for you, in a way, by automating those searches.
And then, there's a project called OSINT-SAP. This is a free OSINT framework that gives people a way to quickly find information and, you know, de-anonymize internet users. It's designed to help identify people online by piecing together publicly available data. So, you can see, there's a pretty wide array of tools, each with its own special purpose, and they all help people with the different aspects of gathering open source information. These tools are, basically, designed to make the process a bit more efficient, especially for those who are trying to be an OSINT defender on Twitter and other platforms.
Social Media and OSINT Defender Twitter - What is the Connection?
Social media OSINT, sometimes called social media intelligence, is a really big part of this whole field. It's about collecting information, or "intelligence gathering," from social media sites. This includes places like Facebook, and of course, Twitter, and Instagram. These platforms are full of publicly shared details, and if you know how to look, you can find a lot of things that help you understand situations or people better. It's not about spying, you know, but about seeing what's already out there for anyone to view.
For example, if someone posts publicly about their activities or their thoughts, that information becomes part of the open source. An OSINT practitioner, or someone trying to be an OSINT defender on Twitter, might look at these posts to understand a trend, or to verify a piece of information. It's about being able to sift through all that public chatter and find the bits that are useful. This can be for a variety of reasons, from journalism to personal safety, or even just for research. It's a very active area, as a matter of fact, because so many people share so much of their lives on these platforms.
The trick with social media OSINT, however, is that while there's a lot of information, not all of it is reliable. That's where the "defender" part comes in. You have to be pretty careful about what you believe and what you use. It's about using those critical thinking skills to evaluate the source and the content. So, while these sites are a rich source of data, they also require a good deal of caution. It's a bit like looking for a needle in a haystack, where some of the hay might, actually, be fake. You really have to be on your guard, you know.
Public Perceptions of OSINT Defender Twitter Activity
It's interesting how some people react when they hear the word "OSINT." The text says, "Some people see 'osint' and lose their minds, becoming instantly 89% more gullible." This really points to a common issue: a lack of proper understanding about what OSINT actually is. When people don't fully grasp it, they might become overly trusting of anything labeled as "OSINT," or, on the other hand, they might become overly suspicious. Neither of these reactions is particularly helpful, you know.
This kind of reaction can lead to problems, especially when people are looking for an "OSINT defender" on Twitter. If someone is too trusting, they might fall for misinformation or disinformation that's presented as legitimate OSINT. And, you know, it’s pretty easy for some folks to get a "dopamine rush" from what they perceive as uncovering secrets, even if those "secrets" are just made-up stories. This is why it's so important to have a clear head and a bit of skepticism when you're dealing with information that comes from open sources, especially on social media.
The text also mentions a "dork" who is "probably addicted to the dopamine rush he gets every time his." This highlights the human element in all of this. There are people who get a thrill from sharing what they think is new information, even if they haven't verified it properly. This can contribute to the spread of unverified claims, which is, in some respects, a pretty big challenge in the information space today. So, being a good OSINT practitioner, or an OSINT defender on Twitter, means being responsible and not just chasing that feeling of discovery without proper checks.
Legitimacy of OSINT Defender Twitter Accounts
There's a pretty important warning out there about Twitter OSINT accounts. The text clearly states, "Please be aware, several of these twitter osint accounts popping up in posts here are not legitimate and instead promote dis/misinformation." This is a big deal, because if you're trying to find reliable information, you need to know who you can trust. It means that just because an account has "OSINT" in its name or talks about OSINT, it doesn't mean it's actually doing good, honest work. You really have to be discerning, you know.
It goes on to say, "The most popular osint accounts on twitter are just tweeting anything they see on telegram." This is a pretty telling observation. It suggests that some of these widely followed accounts aren't doing their own careful research. Instead, they might just be re-sharing information that they find on other platforms, like Telegram, without checking if it's true or not. This is a problem because it can quickly spread false or misleading information to a very wide audience. So, for anyone looking for an OSINT defender on Twitter, this is a very important point to consider.
The community around OSINT is quite large, with, for example, "89k subscribers in the osint community" mentioned. This shows that there's a lot of interest in this field. However, this large community also needs to be careful about what it promotes. It's a shared responsibility to make sure that the information being passed around is as accurate as possible. So, if you're following these accounts, it's pretty much on you to do a little extra checking, too, and not just take everything at face value, which is, in a way, what being a good OSINT defender on Twitter is all about.
Finding Information on Twitter for OSINT Defender Twitter Tasks
One of the classic ways people used to find information online was through something called "Google dorking techniques." This involved using special search terms to get very specific results from search engines. However, the text mentions, "I’m giving an osint presentation and google dorking techniques are no longer working to search x / twitter." This suggests that the ways we search for information, especially on platforms like Twitter, are always changing. What worked yesterday might not work today, which is, honestly, a bit frustrating for people who rely on these methods.
The question is then posed: "Is this the case for all of you?" This indicates that people in the OSINT community are constantly sharing their experiences and trying to figure out what still works. It's a collaborative effort to keep up with the changes in how information can be found. Despite these challenges, the text does confirm that "There are still tweets and historical" information available. So, while the methods might change, the data itself is still there, just perhaps a little harder to get to. It means you have to be pretty adaptable if you want to keep finding things, you know.
Someone also built a tool to help with this, saying, "Hi everyone, i built a quick tool to find tweets based on a location." This is a pretty neat example of how people are creating solutions to ongoing problems. The person mentioned that they "continually had to switch between tabs to get" the information they needed, which suggests that their new tool makes the process much smoother. This kind of innovation is really important for people doing OSINT work, especially when they are trying to be an effective OSINT defender on Twitter, because it helps them gather specific details more efficiently. It's about making the work a little less cumbersome, basically.
Tracking Accounts and OSINT Defender Twitter Tips
Sometimes, people have very specific assignments that involve OSINT. For instance, someone asked, "Hello i have an assignment to track a twitter account, and potentially find out who the owner of the page is." This is a pretty common kind of task in OSINT. It involves looking at all the public information related to a specific account to try and piece together who might be behind it. It's a bit like being a digital detective, trying to find clues that are left out in the open, which, in some respects, can be a really interesting challenge.
The person then asks for recommendations: "What tips/tools would you recommend for a first time osint." This shows that people are looking for guidance, especially when they are just starting out. For someone new to this, it can feel a bit overwhelming, you know, because there's so much information and so many different ways to approach it. The key here is often to start small, focus on publicly available information, and use tools that are known to be reliable. It's about building up your skills step by step, rather than trying to do everything at once.
It's also worth noting that OSINT can be applied to many different kinds of situations. The text mentions, "U.s defense officials are reported that in addition to the aerovironment built switchblade 300 tactical kamikaze loitering munition that the u.s is." While this specific detail about defense is a bit different from tracking a Twitter account, it shows how open source intelligence is used in very serious contexts, too. Information that is publicly available, even if it seems small, can be part of a much bigger picture. So, whether you're trying to track a social media account or understand broader events, the principles of gathering and verifying open source information remain pretty much the same. It's all about being a careful and thoughtful information gatherer, which is, you know, a pretty valuable skill.
Related Resources:

Detail Author:
- Name : Annabel Doyle
- Username : grant.earline
- Email : schiller.stacey@schultz.com
- Birthdate : 1982-12-25
- Address : 7168 Seth Village New Delfinaland, TN 06613-7040
- Phone : +1.704.632.4321
- Company : Huel Ltd
- Job : Copy Writer
- Bio : Omnis in occaecati ipsam sapiente quia fugiat. Ut fuga ipsa deserunt ratione voluptatum veritatis. Necessitatibus mollitia nulla veniam magni sint quo.
Socials
tiktok:
- url : https://tiktok.com/@hettingert
- username : hettingert
- bio : Sit sint reprehenderit possimus autem est ducimus nemo repudiandae.
- followers : 6756
- following : 856
twitter:
- url : https://twitter.com/ted_hettinger
- username : ted_hettinger
- bio : Recusandae repudiandae nulla non aperiam vitae rerum provident. Ut aspernatur voluptatum laudantium reiciendis. Deleniti quidem totam animi asperiores.
- followers : 2257
- following : 430
facebook:
- url : https://facebook.com/thettinger
- username : thettinger
- bio : Neque veniam et sed illo quia quos officia.
- followers : 3018
- following : 805